Life is a journey, not a race!
enjoy the journey
How to configure IPsec VPN tunnel between vCloud Director Edge Gateway and Fortigate Firewall
Overview
VMware Cloud Director supports the following types of site-to-site VPN:
- Another edge gateway in the same organization
- An edge gateway in another organization
A remote network offering IPsec VPN endpoint capability
Depending on the type of connection required, you'll need to complete IP addressing for both ends, together with a shared secret, and indicate which VDC networks are allowed to connect to the VPN link.
Configuring edge gateway IPsec VPN settings
- In the VMware Cloud Director Virtual Data Center dashboard, select the VDC in which you want to configure IPsec VPN.
- In the left navigation panel, under Networking, select Edges.
- On the Edge Gateways page, select the edge that you want to configure and click Services.
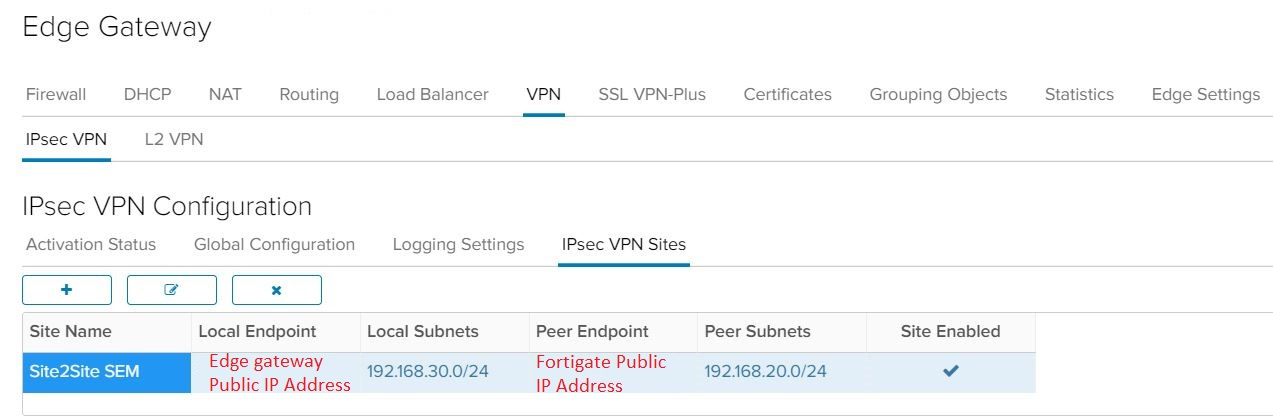
- On the Edge Gateway page, select the VPN tab, then the IPsec VPN tab.
- Select the IPsec VPN Sites tab.
- Click the + button.
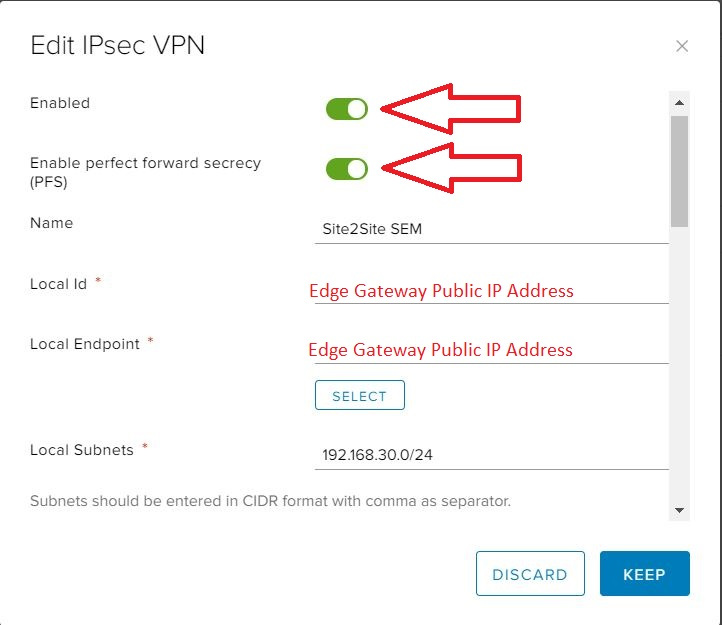
- In the Add IPsec VPN dialog box, select the Enabled option.
- Select the Enable perfect forward secrecy (PFS) option if you’re on-premises/remote site has that capability.
- In the Name field, enter a name for your IPsec VPN.
- The Local ID field is usually set to the same value as the Local Endpoint (see next step).
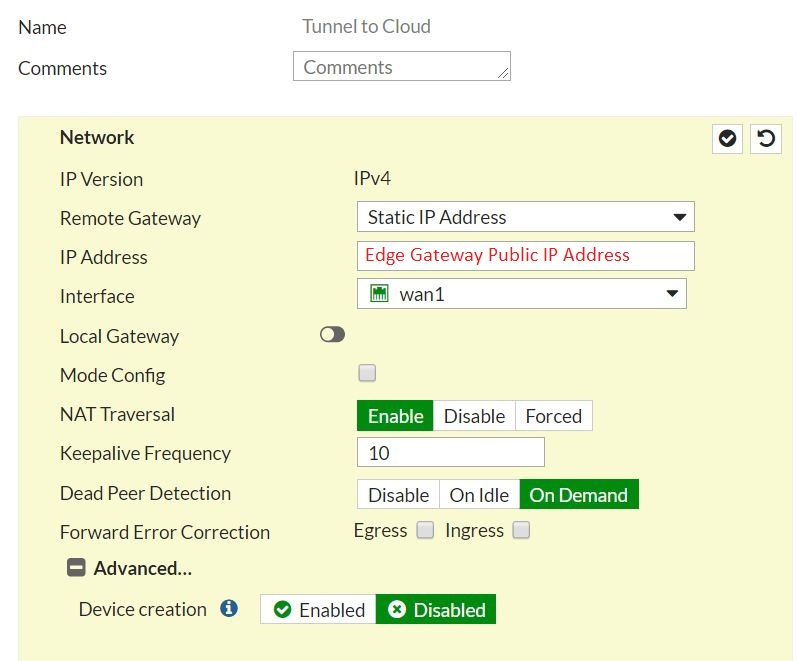
- In the Local Endpoint field, enter the external IP address of your edge gateway (as noted in the Prerequisites).
- In the Local Subnets field, enter the organization networks that can be accessed via the VPN from the remote location. If you enter multiple local subnets, separate them with commas.
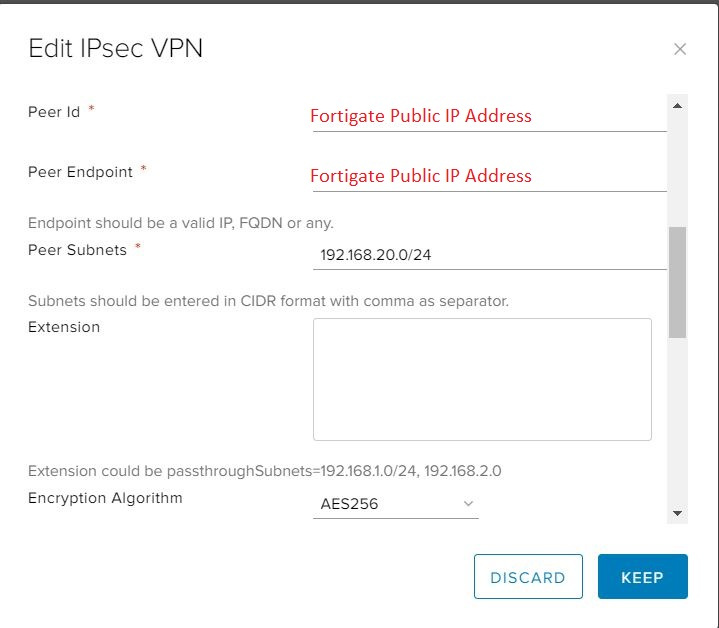
- The Peer ID field is usually set to the same value as the Peer Endpoint (see next step).
- In the Peer Endpoint field, enter the external IP address of your remote site or on-premises firewall or edge where the VPN is being set up.
- In the Peer Subnets field, enter the local subnet of your remote network that you want to access from your Cloud VDC. If you enter multiple subnets, separate them with commas.
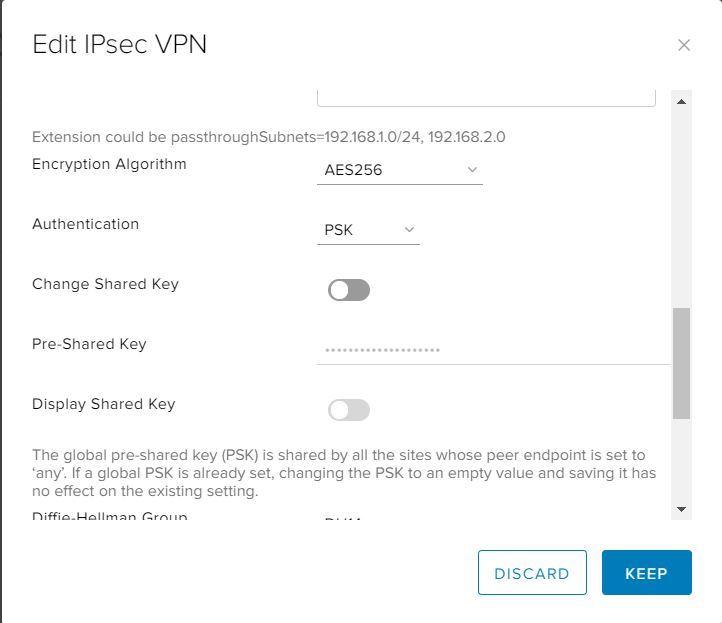
- From the Encryption Algorithm list, select the most secure protocol that is supported by your on-premises gateway.
- From the Authentication list, select the authentication method that is supported by your on-premises gateway. If you want to use certificates, you need to configure those first on the Certificates tab.
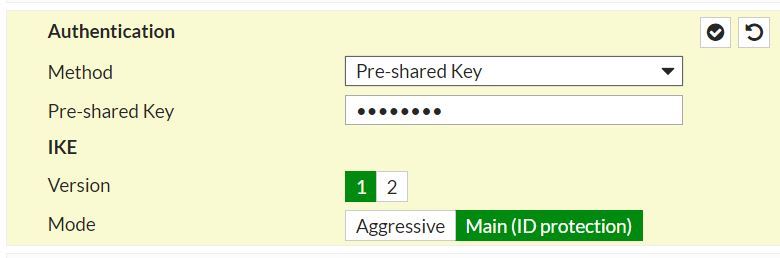
- If you selected PSK as the authentication method, enter the shared secret used to authenticate and encrypt the connection. It must be an alphanumeric string between 32 and 128 characters that include at least one uppercase letter, one lowercase letter, and one number. This must be the same on both sites.
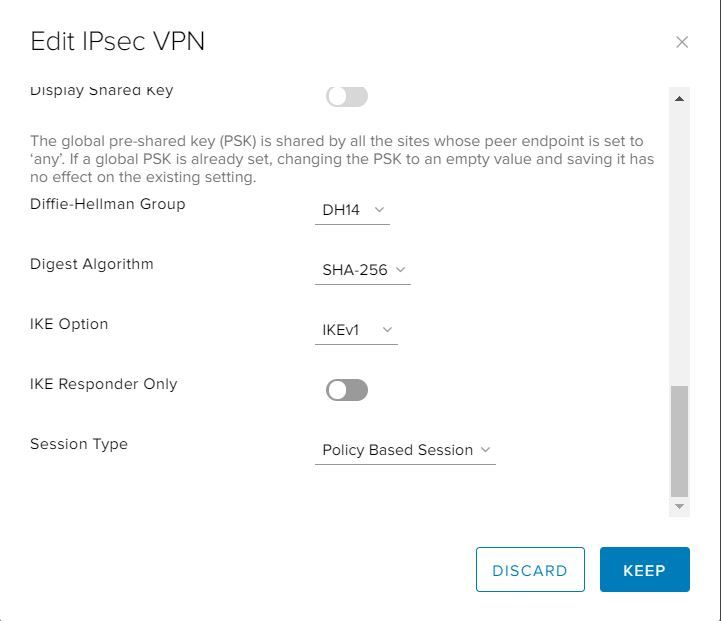
- We recommend setting the Diffie-Hellmann Group to DH14 or higher if you’re on-premises environment can support it.
- When you're done, click Keep to create the edge end of the VPN tunnel.
- Select the Activation Status tab and select the IPsec VPN Service Status option.
IKE Phase 1 and Phase 2
IKE is a standard method for arranging secure, authenticated communications.
Phase 1 parameters
Phase 1 sets up mutual authentication of the peers, negotiates cryptographic parameters, and creates session keys. The supported Phase 1 parameters are:
- Main mode
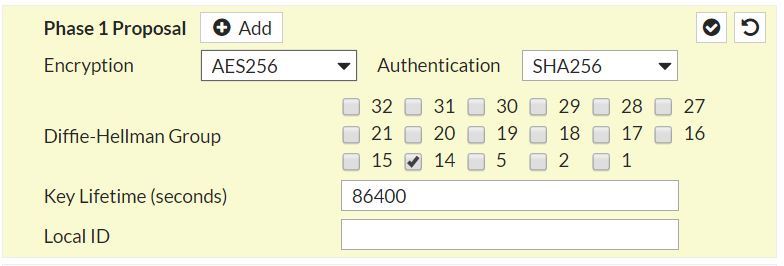
- AES/AES256/AES-GCM (user configurable)
- Diffie-Hellman Group
- Pre-shared secret (user configurable)
- SA lifetime of 28800 seconds (eight hours) with no kilobytes rekeying
- ISAKMP aggressive mode disabled
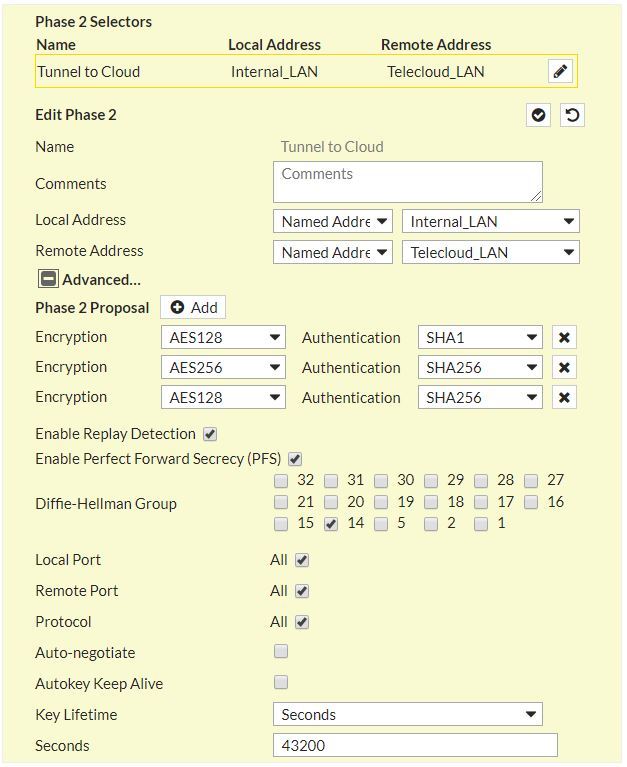
Phase 2 parameters
IKE Phase 2 negotiates an IPsec tunnel by creating keying material for the IPsec tunnel to use (either by using the IKE phase 1 keys as a base or by performing a new key exchange). The supported IKE Phase 2 parameters are:
AES/AES256/AES-GCM (Will match the Phase 1 setting)
- ESP tunnel mode
- Diffie-Hellman Group
- Perfect forward secrecy for rekeying (only if it was switched on in both endpoints)
- SA lifetime of 3600 seconds (one hour) with no kilobytes rekeying
- Selectors for all IP protocols, all ports, between the two networks, using IPv4 subnets.
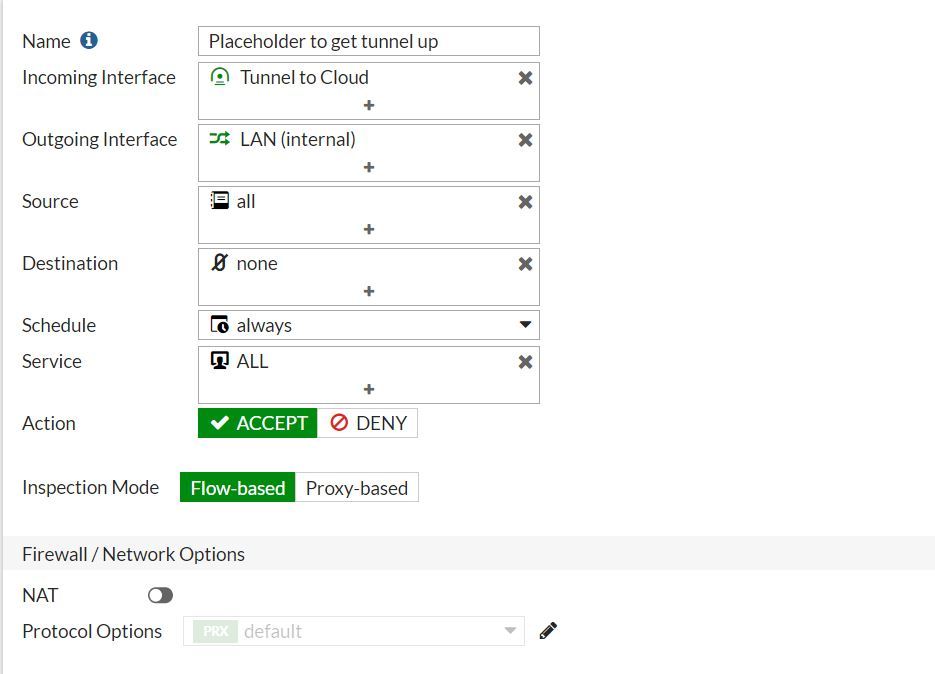
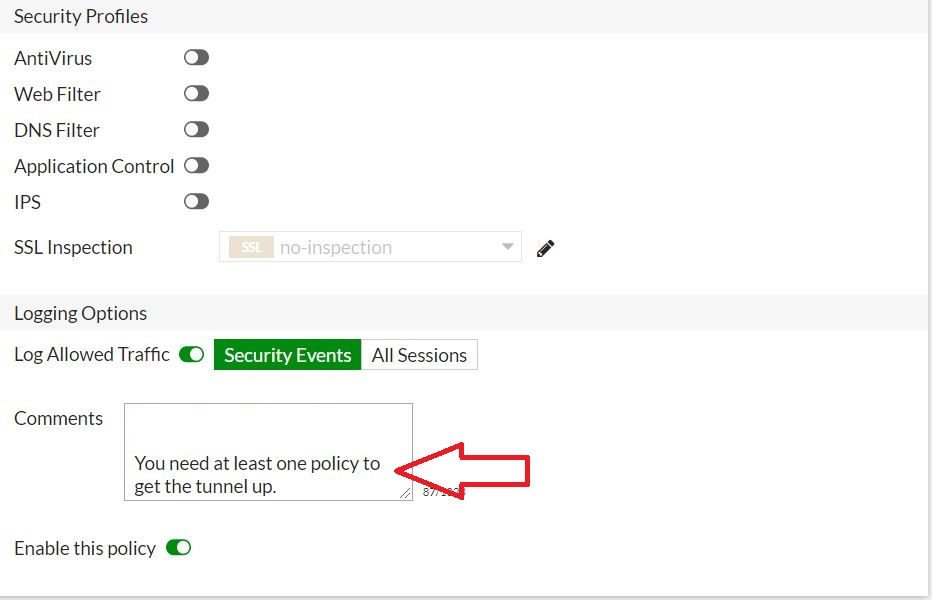
Configuring the edge gateway firewall
When the VPN tunnel is up and running, you'll need to create firewall rules on the edge gateway for any traffic passing over the tunnel
Key points to note:
- You need to create a firewall rule for both directions, that is, from the data center to VDC and from VDC to data center.
- For a data center to VDC, set:
Source as the source IP range for your external VDC/data center network
Destination as the destination IP range for your VDC network
- For VDC to the data center, set:
Source as the source IP range for your VDC network
Destination as the destination IP range for your data center/VDC network
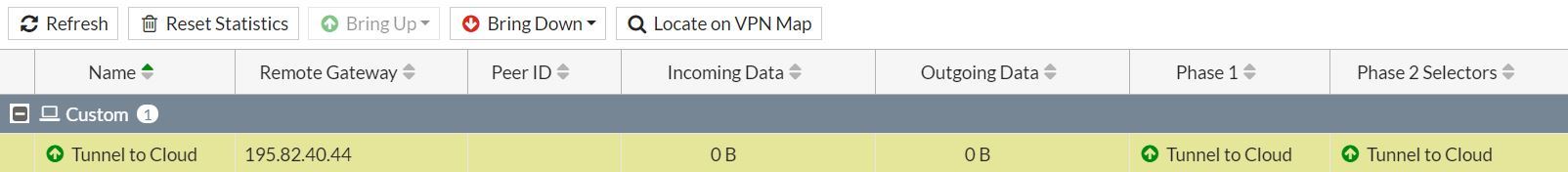
Validating the tunnel
When you've configured both ends of the IPsec tunnel, the connection should start without any issues.
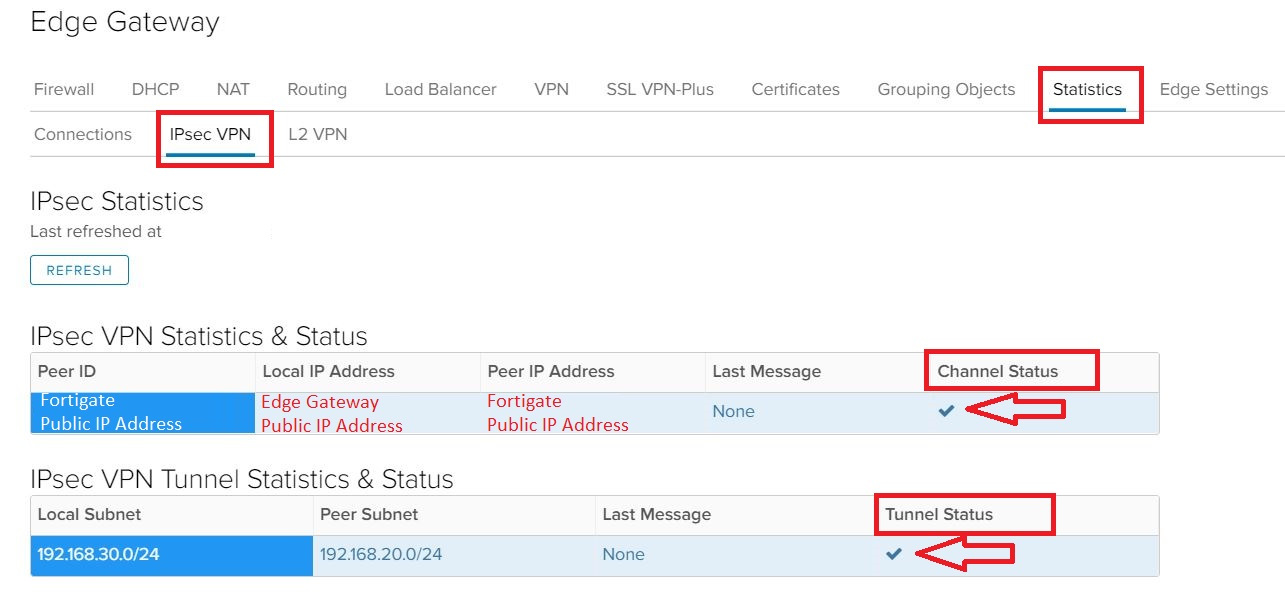
To verify the tunnel status:
- On the Edge Gateways page, select the edge that you want to validate and click Services.
- Select the Statistics tab and then the IPsec VPN tab.
- For each configured tunnel, if you can see a tick, the tunnel is up and running and operational. If any other status is shown, you'll need to review your configuration and any firewall rules.
- You should now be able to send traffic via the VPN.
For better understanding, follow the pictures, we used Fortigate as Customer side:
Good luck!

© 2020 cloudhba.com